In my previous blog post, I showed you how to create an AWS account. However, it’s crucial to take steps to secure your account and prevent it from being targeted by malicious attacks.
In this blog, I will discuss the security measures that you should implement before using AWS services. These measures are highly recommended to ensure the safety and protection of your account.
AWS PROVIDES TWO TYPES OF USER ACCOUNT
✅IAM (Identity and Access Management) user accounts
✅ Root user accounts
IAM USER ACCOUNT
IAM is a web service that allows users to manage access to AWS resources, and IAM user accounts are resources within IAM that represent individuals or applications that interact with AWS services. These users are assigned specific permissions and access to specific AWS resources, which can be controlled and restricted by the account owner.
ROOT USER ACCOUNT
The root user is the highest level of privilege in an AWS account and has complete control over all AWS resources and services. It is created automatically when setting up an account and can perform administrative tasks such as creating, modifying, or deleting IAM users and roles, and accessing billing information. However, it is not recommended to use the root user for everyday tasks due to security risks. Instead, creating an IAM user with appropriate permissions for regular tasks is advisable to reduce potential damage in case of credential compromise.
LET’S TAKE AN EXAMPLE TO BETTER UNDERSTAND THE FUNCTIONALITIES OF BOTH THE ACCOUNTS -:
When you sign up for AWS, it’s important to avoid using or sharing the main account you create by default. This account has full power and control over all the resources and services within the account. To mitigate risks, it’s recommended to create IAM (Identity and Access Management) user accounts that act as subaccounts with limited access and permissions.
For instance, let’s say you create an AWS account named XYZ for your organization(Root account). You also create an IAM user account named ABC, which has its own set of login credentials. The root user can assign ABC limited permissions to access certain services or resources, which provides greater security and control over the account.
Whenever ABC logs in, they must use their own authentication credentials provided by the root user, which is their identity, this is why it is called Identity and Access Management because it manages user identities and controls their access to services and resources.
It’s a best practice to grant limited permissions to IAM users to ensure tighter security over your AWS account.

Identity and Access Management (IAM) is a feature in AWS that provides many benefits, especially for beginners. Here are some of the key advantages:
Granular Access Control: With IAM, you can control who can access your AWS resources and what they can do with them. You can create specific rules that limit access to certain resources and actions, which adds another layer of security to your account.
Centralized User Management: IAM simplifies user management by providing a single location to create, manage, and delete user accounts. This means you can easily add or remove access to AWS resources as needed.
Enhanced Security: IAM provides security features such as multi-factor authentication (MFA), password policies, and security keys to protect your AWS resources and services from unauthorized access.
Auditability and Compliance: IAM enables you to monitor user activity, so you can see who is accessing your AWS resources and what they are doing with them. This helps you meet regulatory requirements and identify potential security risks.
By using IAM in AWS, you can control and manage access to your resources and services while keeping them secure and compliant with regulations.

Here are the key components of IAM in AWS:
Users: A user is an entity that can access your AWS resources and services. Users can be humans, services, or applications.
Groups: A group is a collection of users who have the same permissions. You can create policies and attach them to groups, making it easier to manage access to AWS resources for a large number of users.
Roles: A role is an AWS Identity and Access Management (IAM) entity that defines a set of permissions for making AWS service requests. A role is not associated with a specific user or group; instead, it can be assumed by anyone who needs it.
Policies: A policy is a document that defines one or more permissions. Policies can be attached to users, groups, or roles to specify the level of access they have to AWS resources and services.
Permissions: It defines what a user, group, or role can and cannot do with AWS resources and services.
📌BELOW ARE EXAMPLES OF GROUPS FORMATION, USERS IN MULTIPLE GROUPS AND SINGLE USERS WITHOUT GROUPS.
✅ Multiple groups consist of users — ALICE, BOB AND CHARLES(DEVELOPER GROUP), DAVID AND EDWARD(OPERATION GROUP).
✅ One user in a different group — DAVID AND CHARLES.
✅ Single user without a group — FRED.
NOTE -: THE USER DON’T NECESSARILY HAVE TO BELONG TO A GROUP, AND THE USER CAN BELONG TO MULTIPLE GROUPS.

IAM: PERMISSIONS
In AWS Identity and Access Management (IAM), users or groups can be assigned policies. These policies are JSON documents that define the permissions of the users, specifying which AWS resources they can access and what actions they can perform on those resources.
To follow the least privilege principle in AWS, users are given only the permissions they need to perform their job functions. This minimizes the risk of unauthorized access to sensitive data or resources.
In other words, IAM policies enable fine-grained control over the permissions assigned to users or groups, ensuring that they can access only what they need to perform their job functions. This approach helps to minimize the risk of accidental or intentional data breaches and improves the overall security of the AWS environment.
IAM POLICIES INHERITANCE

IAM POLICIES STRUCTURE
IAM policies have a particular structure that comprises of the following elements:

Version: This specifies the policy language version and should always include “2012–10–17.”
Id: This is an optional identifier for the policy that helps to distinguish between different policies in the same IAM account.
Statement: This element contains one or more individual statements that define the permissions granted or denied by the policy.
Statements: A statement consists of the following elements:
a. Sid: An optional identifier for the statement that helps to manage statements within a policy.
b. Effect: This specifies whether the statement allows or denies access to the resources defined in the policy. The values can be “Allow” or “Deny.”
c. Principal: This element specifies the account/user/role to which this policy applies. It is used to define permissions for specific users or groups.
d. Action: This is a list of actions that this policy allows or denies. It defines the specific operations that are permitted or prohibited for the resource.
e. Resource: This is a list of resources to which the actions specified in the policy apply. It can be used to define specific AWS resources, such as S3 buckets or EC2 instances.
f. Condition: An optional element that defines conditions for when the policy is in effect. It can be used to define restrictions on the policy based on factors such as time of day or location.
IAM — Password Policy
✅ Strong passwords = higher security for your account
✅In AWS, you can setup a password policy:
✅Set a minimum password length
✅ Require specific character types:
<< including uppercase letters
<< lowercase letters
<< numbers
<< non-alphanumeric characters
✅ Allow all IAM users to change their own passwords
✅Require users to change their password after some time (password expiration)
✅ Prevent password re-use
MULTI-FACTOR AUTHENTICATION — MFA
Multi-Factor Authentication (MFA) is a security feature that adds an extra layer of protection to your AWS account.
MFA = PASSWORD YOU KNOW + SECURITY DEVICE YOU OWN

MFA is particularly important for protecting your Root Accounts and IAM users, as these users have access to your account and can potentially change settings or delete resources. By requiring users to enter a code from their security device in addition to their password, MFA significantly reduces the risk of unauthorized access to your account.
One of the main benefits of MFA is that it can protect your account even if your password is stolen or hacked. Because an attacker would need to have both your password and your security device to access your account, the likelihood of a successful attack is significantly reduced. This makes MFA a valuable security feature that can help keep your AWS resources safe from unauthorized access.
IAM ROLES
ONE OF THE IMPORTANT IDENTITIES OF IAM
IAM (Identity and Access Management) Roles for Services are used to grant permissions to AWS services, allowing them to perform actions on your behalf securely. This approach is safer than sharing access keys because it reduces the risk of accidental exposure or misuse.
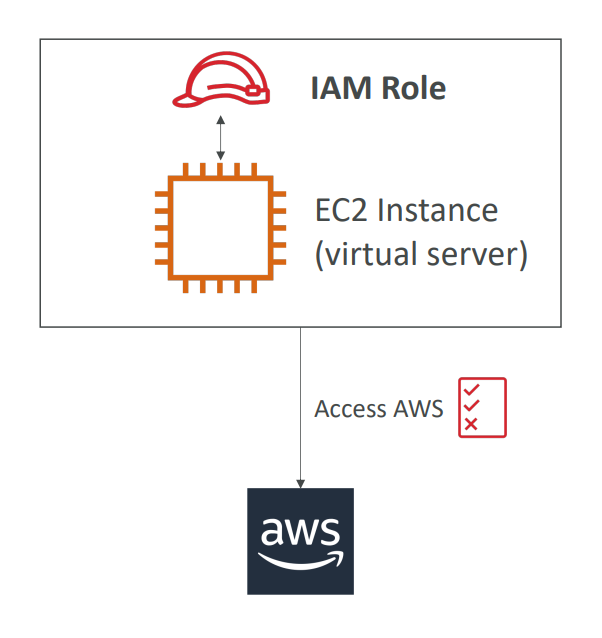
Some of the most commonly used roles for services include EC2 Instance Roles, Lambda Function Roles, and Roles for CloudFormation. EC2 Instance Roles enable services running on EC2 instances to access other AWS services like S3 or DynamoDB. Lambda Function Roles provide permissions to Lambda functions to access AWS resources, while Roles for CloudFormation allow CloudFormation to manage resources on your behalf.
By assigning permissions to IAM Roles, you can ensure that AWS services have the appropriate access to perform their intended actions while maintaining the security of your resources. Moreover, IAM Roles for Services simplify the management of permissions, reducing the need to create and manage multiple sets of access keys.
“I want to clarify that you do not need to worry about some of the names used in this blog post that may be unfamiliar to you. In my upcoming blog posts, I will be covering AWS services one by one and explaining what each service does in detail.”
INTERACT WITH AWS CLOUD
There are three ways to interact :
- AWS Management Console (protected by password + MFA)
<< this is just a graphical user interface, mainly used by the beginners in cloud.
2. AWS Command Line Interface (CLI): Protected by access keys
<< mainly used by Cloud professionals.
3. AWS Software Developer Kit (SDK) — for code: Protected by access keys
<< mostly used by developers through web apps and mobile apps.
NOTE -: THE ACCESS KEYS REFERRING TO ABOVE ARE GENERATED THROUGH THE AWS CONSOLE.

USER MANAGE THEIR OWN ACCESS KEYS.
ACCESS KEYS ARE SECRET, JUST LIKE PASSWORDS.
(DON’T SHARE THEM)
IT’S JUST LIKE,
✅ACCESS KEY — USERNAME
✅SECRET ACCESS KEY — PASSWORD (WHICH YOU WILL GET AUTOMATICALLY AFTER YOU GENERATE YOUR ACCESS KEY)
IAM SECURITY TOOLS
AWS provides two security tools for managing user access and permissions within the IAM service:
IAM Credentials Report (account-level) generates an account-level report of users and their credential statuses, including passwords and access keys, to identify potential security risks.
IAM Access Advisor (user-level) provides a user-level view of their service permissions and access history, ensuring proper permissions and preventing unauthorized access.
These tools enable you to maintain the security and compliance of your AWS environment while granting users the necessary access to perform their tasks.
“Now, you might be wondering how to access these services and their identities. Don’t worry, in my next post, I will provide a hands-on experience and explain everything in detail. I believe that practical experience is essential to truly understand these concepts.
Before ending this post, I want to draw your attention to some IAM guidelines and best practices that will be beneficial for you before starting the hands-on practicals.”
IAM Guidelines & Best Practices
✅Don’t use the root account except for AWS account setup.
✅One physical user = One AWS user.
✅Assign users to groups and assign permissions to groups.
✅Create a strong password policy.
✅Use and enforce the use of Multi Factor Authentication (MFA).
✅Create and use Roles for giving permissions to AWS services.
✅Use Access Keys for Programmatic Access (CLI / SDK).
✅Audit permissions of your account with the IAM Credentials Report
TIPS:_ Never share IAM users & Access Keys.
CONCLUSION
I hope this blog post has provided you with valuable insights into the topic of IAM. From our discussion, we have gained insights into how IAM can help you improve your security stance and streamline the operations of your own AWS account. I encourage readers to keep exploring the topic of IAM and to learn how it can benefit their own AWS accounts.
I want to express my gratitude to the readers for investing their time in reading this post. Your support and feedback are immensely appreciated. If you have any thoughts or suggestions, please feel free to share them in the comments below.
Lastly, if you would like to connect with me on LinkedIn to continue the conversation or to learn more about my experience with this topic, you can find my profile at linkedin.com/in/sahdevgrover
“In the next article, we will dive deeper into IAM (Identity and Access Management) and explore the implementation of the entities we discussed here.”
